In this project, I focussed on Integrity, one of the pillars of the CIA triad, to get a better intuition about this concept. I created a basic File Integrity Monitor FIM in PowerShell to monitor a set of selected files. The FIM detects if any of the files have been altered or deleted or if a new file has been added. If any of these events occur, the FIM raises an alert to inform the user. The application works as follows:
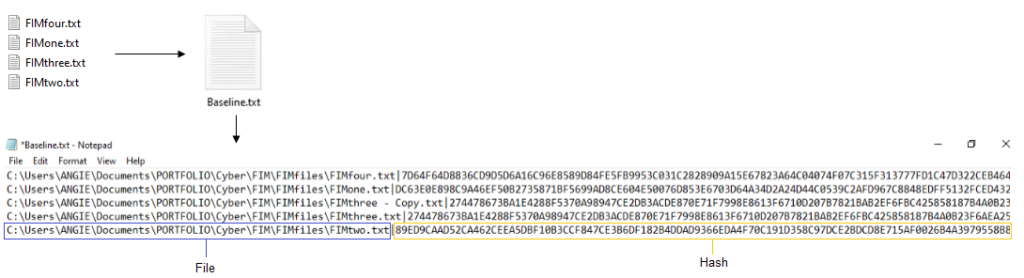
The script prompts the user to choose whether they want to collect a new baseline or monitor files using a saved baseline. If the user selects option one, the script calculates the hash for each file in a specified folder, stores the file path and hash information in a baseline file, and saves it to the specified location.
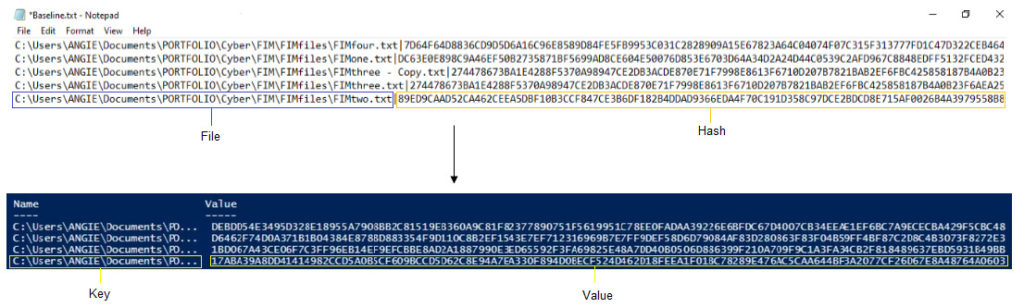
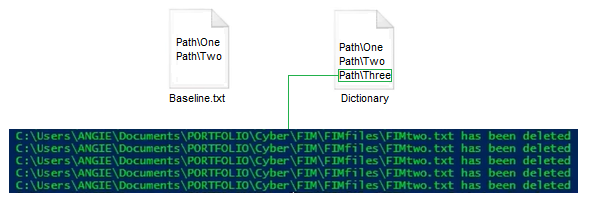
After baseline.txt is created, option two can be selected. the script loads the file path and hash information from the saved baseline file into a dictionary. The file path becomes the key and the hash the value. It then begins to monitor the specified folder for changes.
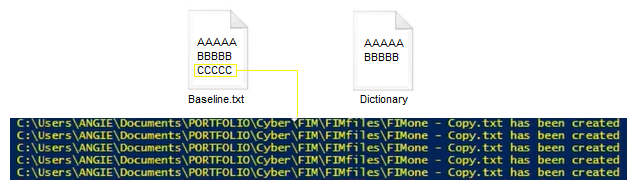
The script checks if new files have been created by comparing the hash of the file to the hashes stored in the dictionary. If the hash does not exist in the dictionary, the script sends a notification that a new file has been created.
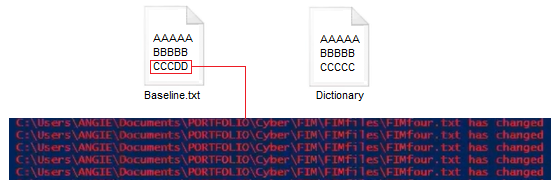
If a file has been modified, the script compares the new hash to the hash stored in the dictionary for that file path. If the hash has changed, the script sends a notification that the file has been modified.
Finally, the script checks if any files have been deleted. It does this by checking the file paths in the dictionary against the current file paths in the folder. If a file path in the dictionary is not found in the current folder, the script sends a notification that the file has been deleted.
Check out the video to see the complete process.
